The Microsoft 365 Suite contains a lot of different solutions; and varying levels of security on those solutions, depending which tier of licensing you have. Microsoft’s security answers have varying levels of user experience, technical requirements, and administrative burdens.
For example, if you’ve used Microsoft native solutions to look at mailflow regularly compared to third-party solutions, you’d probably agree that Microsoft do not provide a quick and easy experience in troubleshooting why an email didn’t arrive. If you have to go back more than 2 days, then you’ll potentially have to wait a few hours just to get the results of the mailflow steps.
Third-party solutions must compete with Microsoft in their own space for security solutions, which means they need to be adding value somehow; cheaper, easier to use, more features, and/or quicker.
Hornetsecurity’s answer to this is their 365 Total Protection solution. I’m fairly experienced with Microsoft’s first party offerings, and a few other third-party mail security solutions, so was interested to see how this stacked up and where it might fit.
Hornetsecurity shows the 3 different tiers of licensing, and an option to start a free trial:


The above pricing based on the feature set seems quite reasonable to me, and from the page you can click on each feature and see more information including a screenshot.
The free trial process is well documented – the first page lays out what you’re in for which will unsurprisingly require tenant admin access to approve tenant permissions for Hornetsecurity.

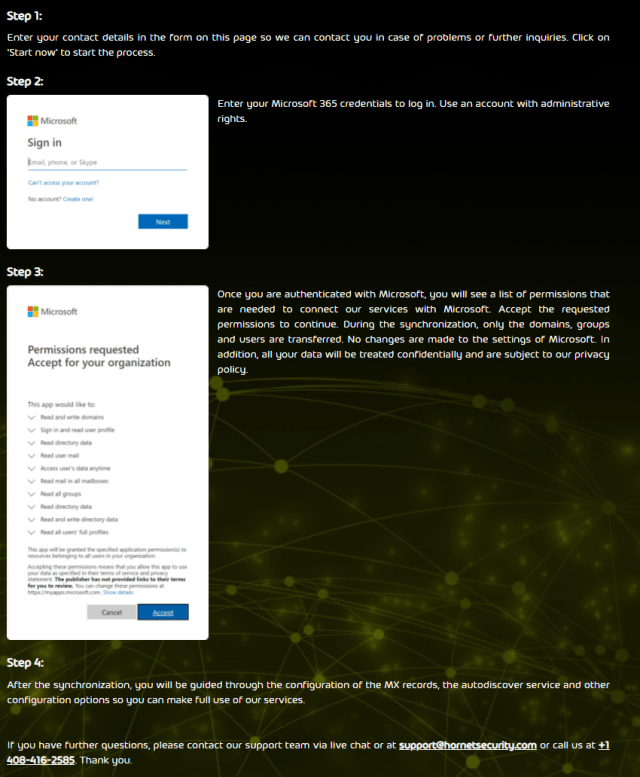
Once you accept the permission request, a synchronisation will start. As I’m doing this in my own tenant of 1 user, it took about 20 seconds to perform. You’ll then need to update MX records so mail flows through the Hornetsecurity service, so it can do many of the services listed.

Not all services rely on mail flow, there is also an Outlook add-in. For older versions of Outlook it can be downloaded and installed like a traditional add-in, or there’s the much nicer modern method that’s controlled from inside Microsoft 365 admin center to deploy and show for users (I wish more vendors did this!).
Either way, the Outlook add-in provides several functions such as being able to report emails, block/allow emails, and view archived emails.
Some other notable features of the 365 Total Protection solution:
- Email Archiving – something Microsoft can do, but don’t do a great job of exposing the archived emails. 10 years of email retention should be more than enough for most companies, and even if you have archiving enabled in your tenant natively, this gives you a backup of all your emails.
- Email Live Tracking – a real time view of mail flow that works quickly and doesn’t require reports to be generated after 2 days that are CSV files.
- Individual User Signatures – Centralised signatures that are also monitored for people who decide to change them away from the company standard. Different groups can get their own style of signature too. Microsoft still has nothing in this space natively and is still in the early days of having a signature saved to someone’s profile.
- eDiscovery – Being able to search quickly across all emails in the company for keywords is a handy thing. Another one that Microsoft can do, but it’s clunky and far from quick.
- Email Continuity Service – If Microsoft’s mail services go down, you can keep going until they’re back – delivering and sending emails directly through Hornetsecurity, then syncing up what happened after the event.
- Automated backups for mailboxes, Teams, OneDrive and Sharepoint – this is really where all your Microsoft 365 data will live. Again, it gives you somewhere this data can be backed up and restored outside of Microsoft’s ecosystem.
There is of course a lot of security aspects to the solution such as Forensic Analyses, URL Malware Control and Realtime Threat Reports, but I quite like the Malware ex-post alert and Malware ex-post deletion. Malicious emails that get through on any system (and I’ve seen this with other third-party solutions as well as Microsoft) need to be detected and cleaned up, as well as investigated on whether anyone clicked the link. This ties into URL Malware control, which will do URL rewriting. Microsoft do this natively, but I’ve found the cleanup aspect can take a little while to perform and isn’t a seamless process from detection to cleanup.
One last point – it is good to see that they have a data centre in Australia as I see many of these companies ignore our region, which makes it hard when you need to keep your data in-country.

I look forward to playing around with Hornetsecurity further. If you’re curious too, then check out their free trial here.













