Right now, it appears that Microsoft Edge is trying to be everything to everyone – which sounds good, until you look at what it could turn into. For enterprise and business, it’s a constantly updated browser that receives frequent Security Baseline recommendations to keep the browser’s settings in line with Microsoft deem as best practise – just like Windows 10/11 and Office apps.
There’s even a ‘Super Duper Secure Mode‘ (which I’m surprised the Microsoft Marketing team approved the name of) which promotes using the browser in the most secure way possible.
Microsoft also provide a fairly open roadmap of upcoming features, and looking for feedback on new items. Check out this list of feedback provided to Microsoft, how long it’s been on their list for, and the status.
The browser itself supports profiles that sign into Azure AD accounts (amongst others) and sync profile data securely to the tenant that account lives in – which can include browser history, favorites, and cached passwords. I’m highlighting here how much trust is put into what Microsoft holds on their business users.
This is the Microsoft I’m a fan of. It’s also why we have openly found out about a new feature currently in canary and dev builds called ‘Buy now, pay later‘. And, it’s also why I’m so disappointed to see this feature, as it flies in the face of what it seems Microsoft is trying to achieve with this trusted, natively embedded in the OS, browser. You can see the angry comments on the TechCommunity post above.
I’d already tweeted my disappointment:
Which lead to a journalist asking for my views for this article:
I’ll try not to repeat what I wrote there, but it sets a precedent of a slippery slope on where the browser ends and third party features start. Microsoft who have become one of the more ‘woke‘ (which I use as a compliment, not an insult) IT companies, should they really be encouraging ‘buy now, pay later‘ to encourage people borrowing money to buy things online?
What I’m really hoping to see is the retraction of this feature, and it’s why I say Microsoft Edge has an identity problem. It can’t be both a consumer and a business/enterprise solution at the same time, if this is the path Microsoft is taking aspects of the browser down. Do we need to have a consumer SKU and an enterprise SKU of the browser? Different installers?
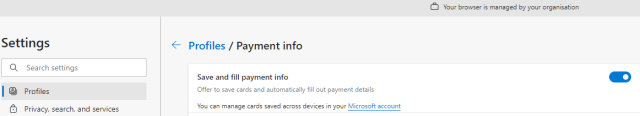
For the particular feature in question, there doesn’t appear to be a way to turn it off specifically. You CAN turn off ‘Save and fill payment info’ which I expect would disable the Zip pay option, but that’s a handy feature you’re removing from users.
Having Candy Crush baked into Windows 10 Home is questionable, but in Windows 10 Enterprise it’s ridiculous (which thankfully it isn’t). However, it’s in Windows 10 Pro…
Am I being too harsh? So many online stores have the Zip pay option on their own store, along with Paypal payment plan options, so does it matter if Edge does it natively too? In my personal opinion it still does matter, because it’s a line that shouldn’t be crossed at all; advertising and the promotion of third party services for profit, native to the trusted browser. If the desktop wallpaper in Windows 10 was changing to promote anything outside of Microsoft services, people would be outraged.
I also expect Microsoft has a reasonable agreement lined up with Zip, which would make reversing this decision harder (or costlier), which will mean they won’t give it up quickly. Historically we have seen Microsoft change direction based on waves of negative feedback – which is awesome – but I’m really unsure if that will be enough this time.
Microsoft needs to decide what Microsoft Edge is. Is it a trusted platform, or is it a vehicle to increase revenue directly through partnerships, making money off the user? If it’s both, then it needs to have a high level switch to allow users and companies to turn off the money making side – especially when we’re already paying for the OS, and the browser is bundled with that.
Edit: I believe this feature will only turn up if you’re signed into the browser’s profile with a Microsoft account – so less of an impact on business users, but the general points still stand. I’ve seen this profile detection behaviour recently, where advertising fo the Microsoft Start app only popped up when I was logged in with a consumer profile, potentially triggered by one of Microsoft’s home pages – having the same home page in an AAD account profile didn’t show: